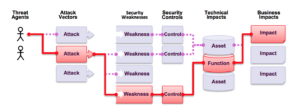
How do I know what kinds of proactive internet security are worthwhile for my software project?
I have been struggling, for years, to find a good answer to this question. This seems like something I could have learned in a graduate course on security, but I’m naive and now that I’m looking for an answer, I cannot find one. Why isn’t there just a pretty diagram showing me what I need to do over at OWASP?
First off, there are countless attack vectors, any software is potentially vulnerable. There are non-technical phishing attacks, attacks on your hardware / bios / OS, attacks over the internet, etc, along with multiple layers of “security” to be applied at every step. Some simple strategies to protect against these attack vectors are obvious, such as only depending software that is not known to have vulnerabilities, updating modules to get bug fixes, etc. Testing for XSS vulnerabilities anywhere a user can input. Firewalls. Password encryption. Fuzzing. Bug bounties. What next? There are hundreds of things you can do, how do you know which ones are enough?
Second, a codebase often has many entry points, more than can be enumerated and more than can be tested. Combining all potential vectors with all potential weaknesses gives a threat agent so many resources and strategies that if someone wants to hack you, it is only a matter of time. Hopefully, the good guys find it and report it first. After the recent articles about Pwn2Own, the security flaws I’ve seen and heard of, and the amount of exploited data the past few years, I figure the best and only perfect way to protect your application is simply to just not have one. Obviously that’s not a possibility, so when have you done enough? How can you balance product against security?
Some security approaches seem almost useless. CSP doesn’t protect against anything in 90+% of cases. Some things are redundant, DNSSEC is meaningless and you should assume that is always insecure. How can I tell what is useful and what is not?
I need help. If someone can tell me what to read to get a clear picture, from an established professional with a good track record, please, please do. If they work at a company that gets hacked or exploited regularly, have they really been doing a good job?
If you feel like this, I’m sure you aren’t alone. While you can never stop someone from trying to get in, there are 2 things to do.
First – purchase active monitoring of your endpoints. Once someone gets in, this will help you get them out. Second – do the basics, get the good guys helping you through bounties, and spend as much time on anti-fraud, marketing, and risk management to make it seem like you are doing a good job. Do everything you can so you don’t seem like an easy target. Remember, in today’s social climate, facts and truth don’t really matter. Maybe it’s more important to seem secure than to be secure.
References
https://deepsec.net/docs/Slides/2016/CSP_Is_Dead,_Long_Live_Strict_CSP!
https://cleantechnica.com/2019/03/25/hackers-walk-away-with-375000-and-a-tesla-model-3
https://medium.com/swlh/what-are-the-best-practices-for-securing-your-saas-application
https://www.sohamkamani.com/blog/2017/01/16/web-security-essentials/
https://sockpuppet.org/stuff/dnssec-qa.html
https://sockpuppet.org/blog/2015/01/15/against-dnssec/
https://en.wikipedia.org/wiki/Web_application_security
https://en.wikipedia.org/wiki/OWASP